
|
|
I basically created this tutorial to both meet a requirement of a college web class and in response to the many mediocre tutorials about user authentication which are available on the web. Most will tell you how to implement basic user authentication, but I haven't seen one yet which actually explains it in terms that most people can understand and learn something from. Hopefully, I've done this a little better than most. Please feel free to give me feedback through the form you will find at the end of the tutorial or by emailing me at the address found at the bottom of these pages. I will try to help you as best I can in making this tutorial better. Plus, who doesn't like feedback about their site? And now, on with the tutorial! |
|
What exactly is user authentication and what is it used for? Perhaps this is best answered by an example. Try going to this URL and watch what happens. Don't worry about the message which follows it; I'm the site administrator. ;-)
|
|
Host restriction is a way to restrict access based on the user's computer "name". This can be either a domain-name or an IP address. An example of a domain name is , your current domain name. An example of an IP address is , your current IP address. If your group members all have their own computers connected to an Ethernet, each will have their own domain-name and IP address which never changes. Thus you can allow only those hosts and perhaps that of your professor (as long as this address is unchanging from login to login) to access the directory. An example of a situation in which this method would not be useful is if one or more group members uses on-campus workstations. Although each computer has its own unchanging domain-name and IP address, there is no guarantee as to which computer the group member will use each time he or she logs in, so restricting their access to a specific domain-name and IP address would not be reliable. Another example would be if a group member uses a dialup service. Each time they connect to the modem pool, they are assigned a different domain-name and IP address based on network traffic. This would be another case in which host restriction would not be a good idea. Password-based authentication would be a better choice in these situations. If you already know what a .htaccess file is, you can proceed to the tutorial on host restriction or you can read about password-based restriction below. You can learn about .htaccess files here . |
|
The other type of user authentication is password-based. When a user tries to go to a URL which is in a password-protected directory, a dialog box will pop up, prompting them to enter a name and password to proceed, similar to the example at the top of this page. If the user fails, they are not allowed access to the directory and an error page is displayed. If they succeed, they are granted access as long as they remain in the same browsing session. That is, as long as their browser program is still running, the server will remember their name and password and grant them access. If you already know what a .htaccess file is, you can proceed to the tutorial on password-based restriction. Otherwise... |
|
Both methods of user authentication require the use of a file known as .htaccess. This is the file which contains the commands that tell the server who to let in and who to turn away. For more info on .htaccess files, proceed to the this section. |
|
|
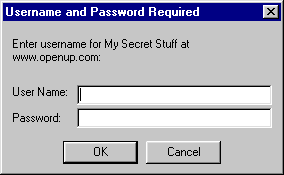 You should get a popup window similar to the one shown here.
What kinds of uses does this have? Suppose you are working on a group project which involves some sort
of web design. You want to be able to let your group see HTML pages in your
project directory, but you want to restrict access to that directory by others who are not in your
group. The solution is relatively easy using a built-in feature with most servers called
user authentication. User authentication allows you to restrict web access by two methods:
host restriction and password-based restriction.
You should get a popup window similar to the one shown here.
What kinds of uses does this have? Suppose you are working on a group project which involves some sort
of web design. You want to be able to let your group see HTML pages in your
project directory, but you want to restrict access to that directory by others who are not in your
group. The solution is relatively easy using a built-in feature with most servers called
user authentication. User authentication allows you to restrict web access by two methods:
host restriction and password-based restriction.